40 security labels access control
Access control - Wikipedia In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process.The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.. Locks and login credentials are two analogous mechanisms … Overview of access control | Cloud Storage | Google Cloud Oct 07, 2022 · ACLs control permissioning only for Cloud Storage resources and have limited permission options, but allow you to grant permissions per individual objects. You most likely want to use ACLs for the following use cases: Customize access to individual objects within a bucket. Migrate data from Amazon S3. Additional access control options
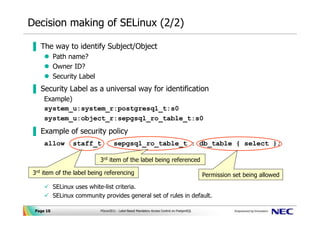
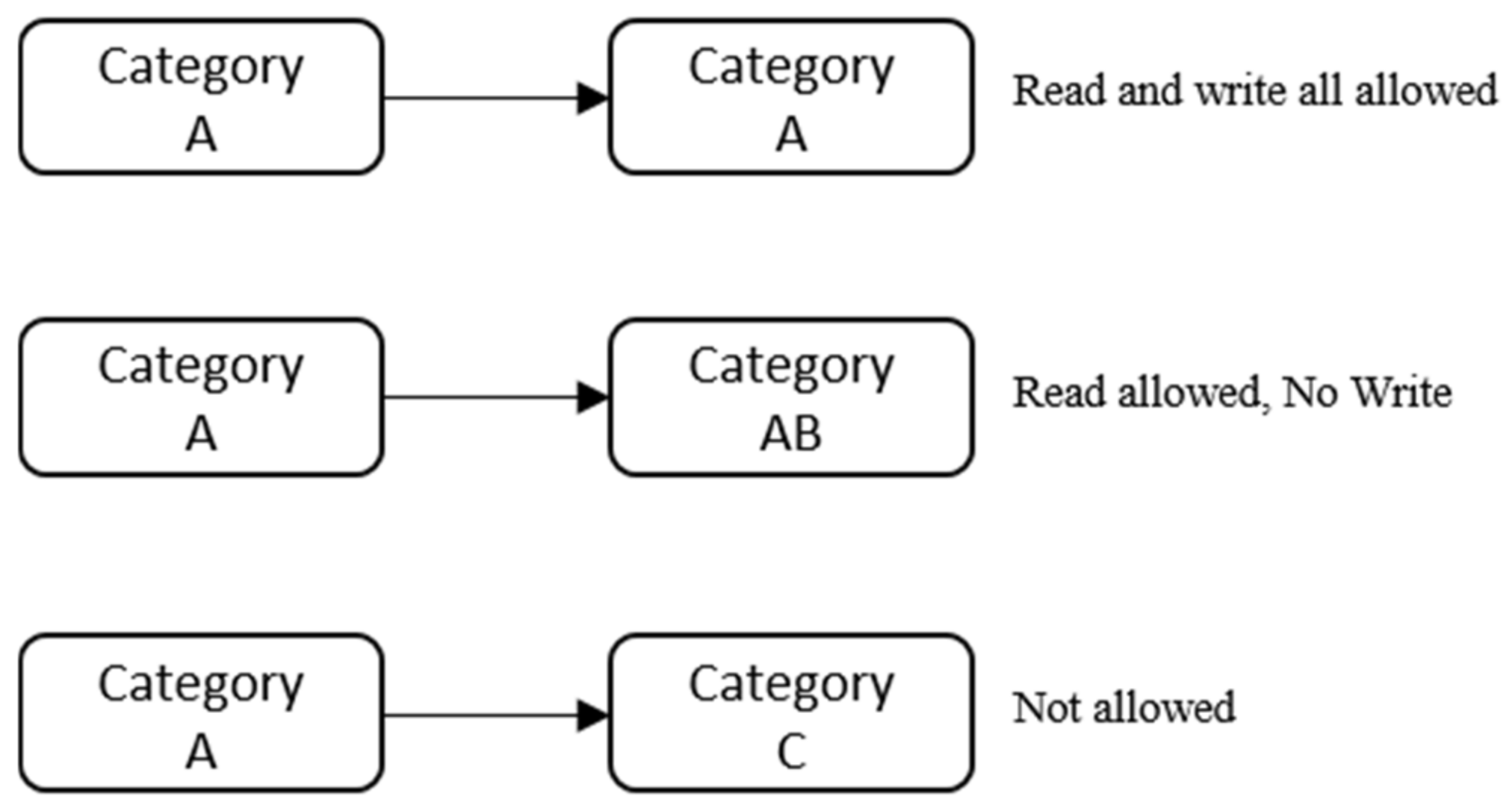
How security labels control access - help.hcltechsw.com Security labels rely on security label components to store information about the classification of data and about which users have access authority. Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES).

Security labels access control
How security labels control access - help.hcltechsw.com Label-Based Access Control You can use label-based access control (LBAC), an implementation of multi-level security (MLS), to control who has read access and who has write access to individual rows and columns of data. Security Control Systems & Equipment in Hodgson MB | YellowPages.ca™ Card Access Systems, Carwash Control Systems, Solar Panel Pay & Display Meters, Gates & Ticket Dispensers, Swing & Slide Gate Operators, Automated Pay On Foot Systems, Car Wash Control Systems, Carwash Counter, Carwash Bay Counter, Parking Meters, Security Gates, Barrier Gates, Automated Parking Systems, Parking Lot Signs, Bollards, Bollard Covers, Parking Curb, Card Access, Parking Lot ... Using Security Labels for Directory Access and Replication Control - Isode The access control model is that a Security Label is associated with each entry in the ...
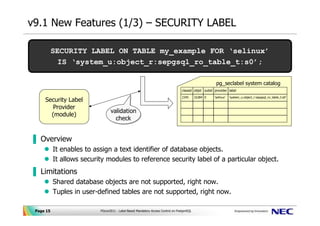
Security labels access control. Security-Enhanced Linux - Wikipedia Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC).. SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions.Its architecture strives to separate enforcement of security … Access Control Systems near Selkirk, MB | Better Business Bureau. Start ... BBB Directory of Access Control Systems near Selkirk, MB. BBB Start with Trust ®. Your guide to trusted BBB Ratings, customer reviews and BBB Accredited businesses. [Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label A PTC Technical Support Account Manager (TSAM) is your company's personal advocate for leveraging the breadth and depth of PTC's Global Support System, ensuring that your critical issues receive the appropriate attention quickly and accurately. Top 20 Access Control Jobs in Selkirk, Manitoba (with Salaries ... Browse 173 SELKIRK, MANITOBA ACCESS CONTROL job listings from companies with openings that are hiring right now! Quickly find and apply for your next job opportunity on Workopolis. Compare salaries and apply for all the access control jobs in Selkirk, Manitoba.
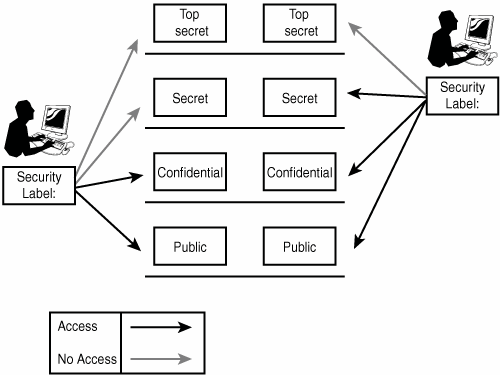
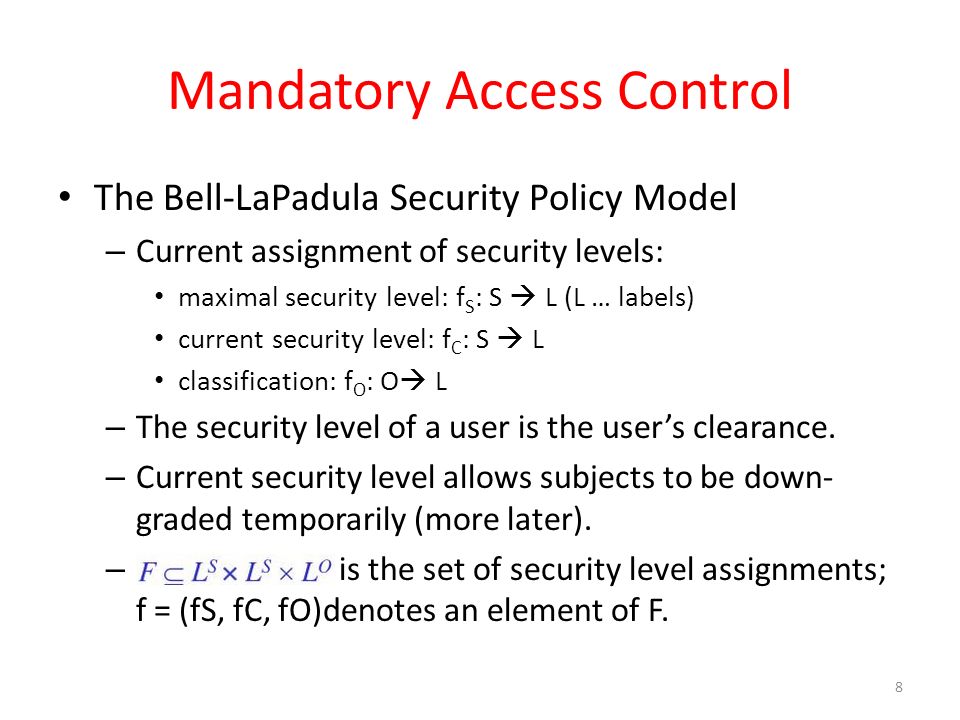
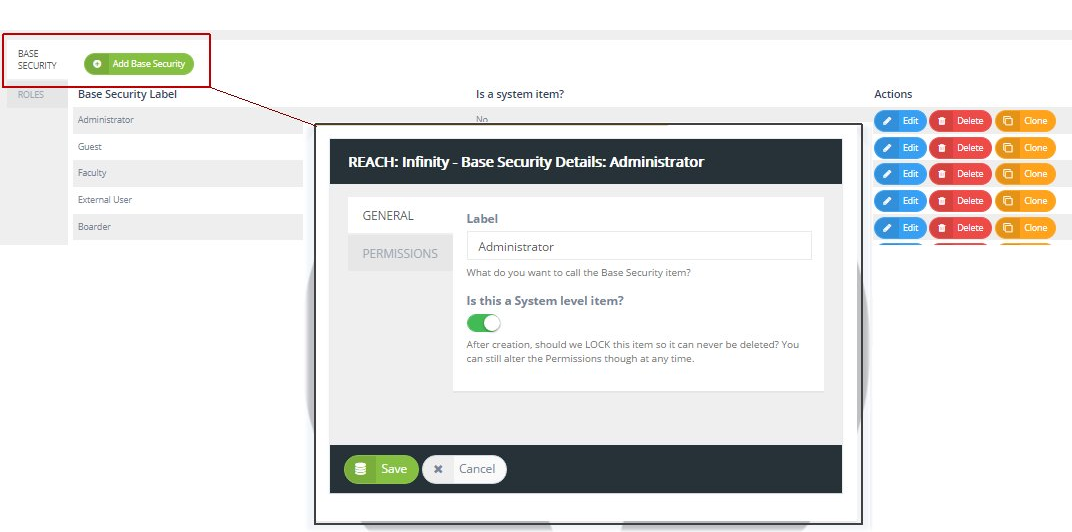
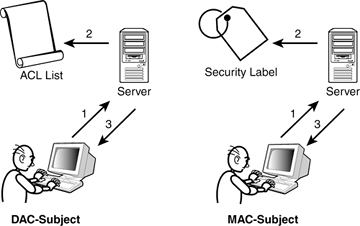
Security Labels and Access Control - support.ptc.com Security Labels and Access Control Security labels are applied in addition to standard Windchill access control policy and ad hoc rules. A security label acts as a gate; if the user is not cleared for the security labels on an object, they cannot access the object, even if their access control permissions would otherwise allow them access. Mandatory access control - Wikipedia In computer security, mandatory access control refers to a type of access control by which the operating system or database constrains the ability of a subject or initiator to access or generally perform some sort of operation on an object or target. In the case of operating systems, a subject is usually a process or thread; objects are constructs such as files, directories, TCP/UDP ports, shared memory segments, IO devices, etc. Subjects and objects each have a set of security attributes. Whene Configure a Security Context for a Pod or Container | Kubernetes Sep 30, 2022 · A security context defines privilege and access control settings for a Pod or Container. Security context settings include, but are not limited to: Discretionary Access Control: Permission to access an object, like a file, is based on user ID (UID) and group ID (GID). Security Enhanced Linux (SELinux): Objects are assigned security labels. Running as … Computer access control - Wikipedia In computer security, general access control includes identification, authorization, authentication, access approval, and audit.A more narrow definition of access control would cover only access approval, whereby the system makes a decision to grant or reject an access request from an already authenticated subject, based on what the subject is authorized to …
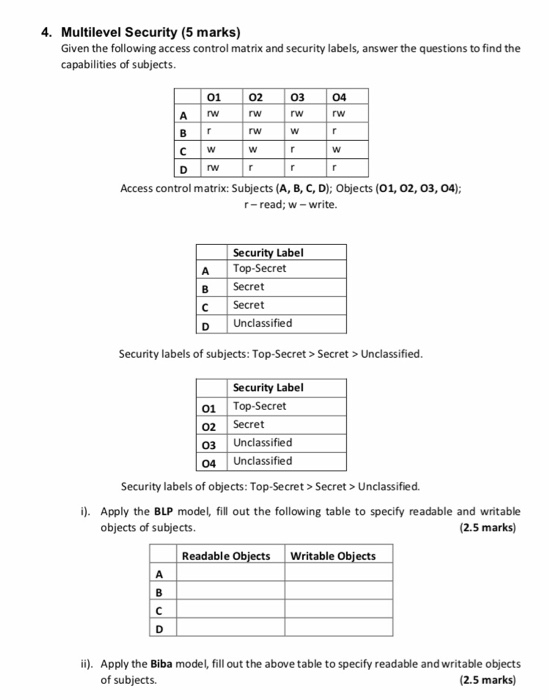
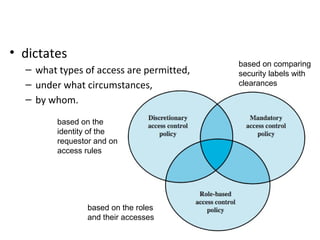
Label-based access control (LBAC) overview - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to data in order to protect the data. They are granted to users to allow them to access protected data. Format for security label values Label Security | Oracle Oracle Label Security Control what data users see based on data and session labels. Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance. Products - Red Hat Customer Portal Engage with our Red Hat Product Security team, access security updates, and ensure your environments are not exposed to any known security vulnerabilities. ... Share, secure, distribute, control, and monetize your APIs on an infrastructure platform built for performance, customer control, and future growth. Product Documentation Product Info ... Access Control Models: MAC, DAC, RBAC, & PAM Explained Mandatory access control uses a centrally managed model to provide the highest level of security. A non-discretionary system, MAC reserves control over access policies to a centralized security administration. MAC works by applying security labels to resources and individuals. These security labels consist of two elements:
Security Labels - PolyLabel.com The main reason why these types of labels are used is to control access to information or certain products. For example, a cargo container will have a security label so that no one can access the materials in that cargo container without the proper authorization.
GNU GRUB Manual 2.06 This means the BSD ‘a’ partition on first PC slice number of the second hard disk. Of course, to actually access the disks or partitions with GRUB, you need to use the device specification in a command, like ‘set root=(fd0)’ or ‘parttool (hd0,msdos3) hidden-’.To help you find out which number specifies a partition you want, the GRUB command-line (see Command-line interface) …
Access control lists (ACLs) | Cloud Storage | Google Cloud Oct 07, 2022 · What is an access control list? An access control list (ACL) is a mechanism you can use to define who has access to your buckets and objects, as well as what level of access they have. In Cloud Storage, you apply ACLs to individual buckets and objects. Each ACL consists of one or more entries. An entry gives a specific user (or group) the ...
Label-Based Access Control - IBM The database security administrator role (DBSECADM) is required to create and maintain label-based access control security objects. Security label components Security label components are security objects for defining security policies. The elements of these components are used to define security labels, which control access to protected tables. Security policies Security policies are database objects that you create and use to protect tables from unauthorized access. Security labels
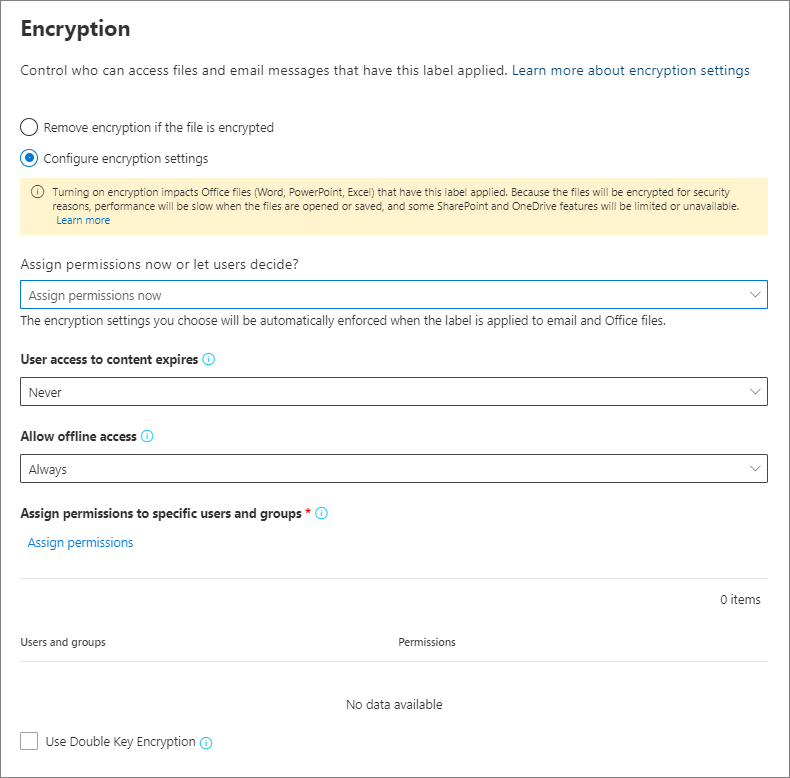
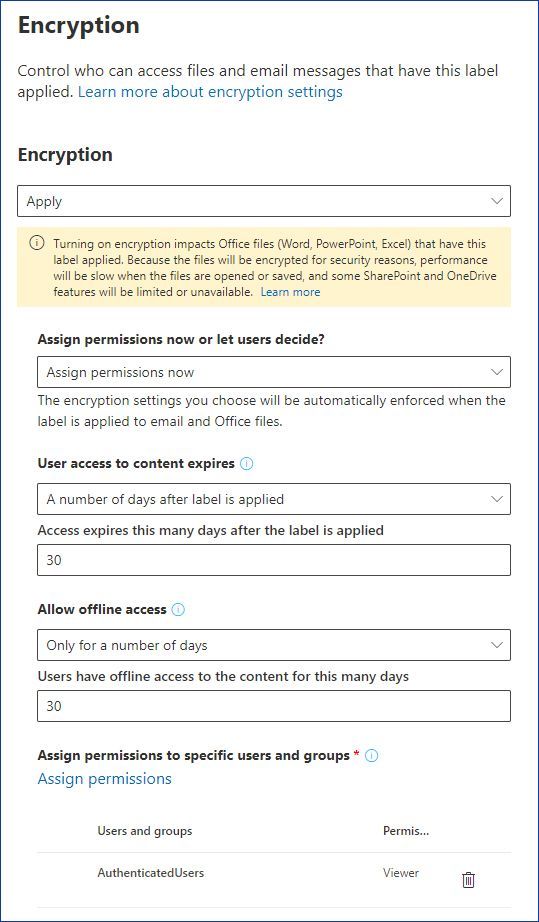
Permissions - Security & Compliance Center - Office 365 Sep 27, 2022 · These people can perform only the tasks that you explicitly grant them access to. To access the Security & Compliance Center, users need to be a global administrator or a member of one or more Security & Compliance Center role groups. Permissions in the Security & Compliance Center are based on the role-based access control (RBAC) permissions ...
Mandatory access control - Wikipedia In computer security, mandatory access control (MAC) refers to a type of access control by which the operating system or database constrains the ability of a subject or initiator to access or generally perform some sort of operation on an object or target. In the case of operating systems, a subject is usually a process or thread; objects are constructs such as files, directories, …

retail security anti-theft 58khz eas soft tag strips sticker am dr label for security door eas am anti theft system(1000 pieces)
Access Control using Security Labels & Security Clearance - Isode Security Labels provide an important mechanism for controlling access to information in many high security environments, and are also useful in environments with lower security requirements. This paper provides a reasonably detailed description of how security labels and clearances work, while attempting to avoid the high level of technical complexity seen in many papers in this area.
Home Security Systems Selkirk, MB - ADT Security Monitoring Affordable Home Security - Free Keychain Remote w/ Panic Button - Helps Protect Your Family and Property While You're Home and Away - Window & Door Protection - Motion Detectors - Loud Sirens - 24/7 Monitoring - Two Way Voice Communication - Fire & Smoke Detection - Emergency Medical Alerts - Great for Single Family Homes, Condos, Town Homes and offices.
Using Security Labels for Directory Access and Replication Control - Isode The access control model is that a Security Label is associated with each entry in the ...
Security Control Systems & Equipment in Hodgson MB | YellowPages.ca™ Card Access Systems, Carwash Control Systems, Solar Panel Pay & Display Meters, Gates & Ticket Dispensers, Swing & Slide Gate Operators, Automated Pay On Foot Systems, Car Wash Control Systems, Carwash Counter, Carwash Bay Counter, Parking Meters, Security Gates, Barrier Gates, Automated Parking Systems, Parking Lot Signs, Bollards, Bollard Covers, Parking Curb, Card Access, Parking Lot ...
How security labels control access - help.hcltechsw.com Label-Based Access Control You can use label-based access control (LBAC), an implementation of multi-level security (MLS), to control who has read access and who has write access to individual rows and columns of data.





















Post a Comment for "40 security labels access control"